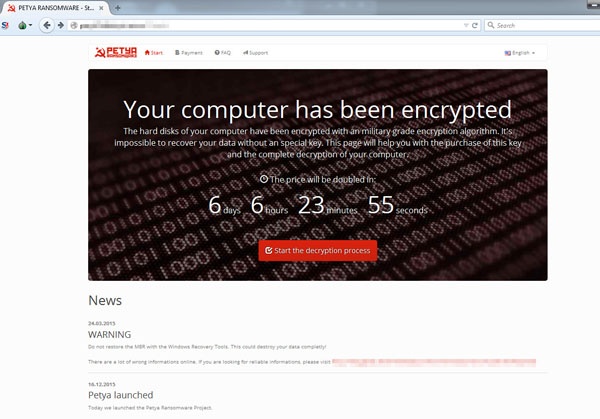
Petya ransomware doesn't simply encrypt files, rather it overwrites the entire Master Boot Record (MBR) and encrypts the Master File Table (MFT). The ransom note comes up at system startup first with an ominous red skull screen. Here is a short video that shows it live:
The actors behind Petya are mainly targeting businesses. Spear phishing emails are sent to company HR departments containing a Dropbox link to a supposed resume. The link goes to an executable file that once opened, crashes and reboots the computer. That's when victims see the skull and crossbones image with a message that the disk is encrypted. The only way to get your data back is by paying the ransom which starts at .99 Bitcoin (around $400), then doubles after one week.
How The Attack Works
Going after the MFT is a fast attack that takes far less time than encrypting data files, but the overall effect is the same – the data becomes inaccessible. F-Secure reported that Petya executes in two stages. The first stage is the main dropper, which:
During the second stage, the machine boots to MBR code, which:
Mischa Ransomware Backup
A new version of Petya was released in May 2017 with a backup ransomware called Mischa. If Petya fails installation because it was stopped at the administrative privileges level, it will install Mischa which only needs standard user privileges to execute. Mischa scans the computer for data files and encrypts them with the AES algorithm and adds an extension to the file name. This ransomware not only encrypts standard file types like PNGs, DOCXs, etc. but also goes after .EXE files. Mischa is more like other ransomware strains, it encrypts the files then demands a ransom of 1.93 bitcoins (about $875).
Another Petya Version Wrapped In Extra Nastiness
PetrWrap is yet another version of Petya uses the PsExec tool to install ransomware on every workstation and server it can access. Instead of using the original Petya code, a special module was created by the group behind this strain that patches the original Petya ransomware 'on the fly', to hide the fact that Petya is handling the infection, and PetrWrap uses its own crypto routines with their own keys.
Once the workstation is infected, the victim ends up with the file system's master file table encrypted with a better scheme than the old Petya used. The PetrWrap coders used a tried-and-true, debugged version of Petya's low-level bootloader, ensuring they had "production-quality" criminal software to make sure their infections would be successful.
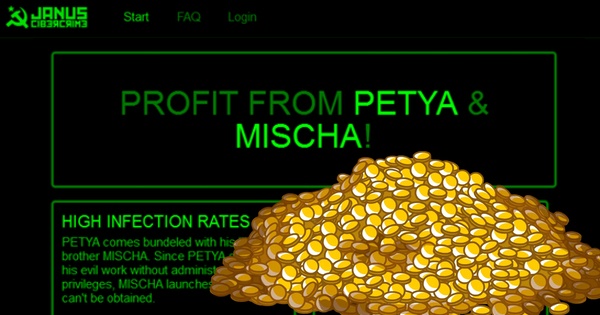
Ransomware-as-a-Service
A Ransomware-as-a-Service offering for Petya/Mischa was launched in July 2017. They pay their distributors a percentage of the ransom received on a scale, say 25% for 5 bitcoins on up to 85% for 125 bitcoins and above.
Petya Decryptor
Currently there is a decryption for Petya, however we know the criminals constantly update their code so it may not last.
