Maktub Locker is a new strain of Russian ransomware written by professionals with experience. They spent a lot of time on the payment website. It is distributed through phishing emails with a .scr attachment appearing to be a Terms-of-Service update. When the attachment is opened, it actually has a (fake) update in .rtf format and right then the ransomware starts to encrypt files in the background. Once encryption is complete, the ransom note comes up:
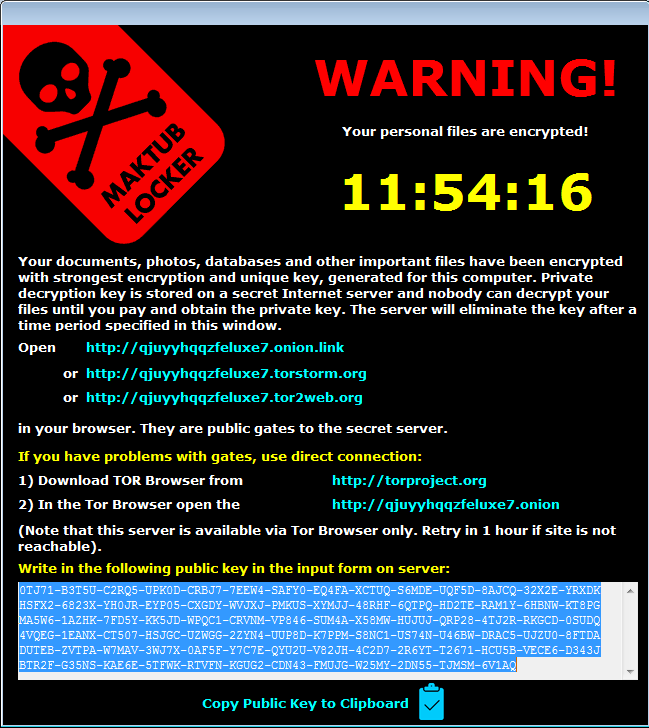
Maktub Locker doesn't require a Command and Control server key to run – the data can also be encrypted offline. This ransomware not only decrypts but also compresses files, most likely to speed up the encryption process It also doesn't use a static extension, each victim has random and unique file extensions. The website is very clean and well designed, using 'polite' language:

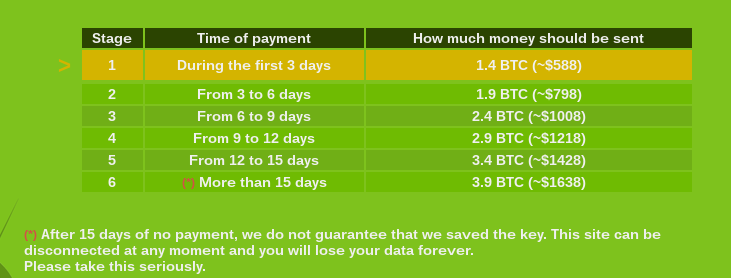
Victims can select up to 2 files to be decrypted for free before payment as a 'guarantee' that payment will give them a key that will decrypt all files. Ransom starts at 1.4 Bitcoin and increases based on how much time has passed, topping out at 3.9 Bitcoins after 15 days. As you can see in the below screenshot they warn that data may be lost forever after 15 days without payment:
Less than a month after Maktub Locker was first seen, a different phishing scam was being sent out with the same infection in the UK. A widespread attack sent victims an email with their actual home address with a message claiming they owe money to British businesses and charities when they do not. A link in the email tells the victims it's where they can view the invoice, once clicked encryption starts. Here is an example of criminals using information from a data breach to social engineer victims on a massive scale. Keep in mind cybercriminals often test new scams in the UK, work out any bugs then launch the same attack in the US.
