Stop Supply Chain Compromise with Defend
Supply chain compromise is on the rise
90%
of organizations have experienced security incidents caused by supply chain weaknesses
50%
of security incidents and data breaches involved stolen credentials
30%
increase in stolen credentials in the last five years
Your supply chain introduces significant risk
A single compromised vendor can result in a high proportion of their customers also becoming compromised, simply because the attacker was able to leverage their trusted relationship as an entry point and socially engineer their victims.
Email threats from compromised accounts have traditionally been hard to detect, but none more so than those from trusted suppliers and business partners. The native security in Microsoft 365 and secure email gateways (SEGs) struggle to detect phishing emails sent from trusted domains, leaving organizations exposed to account takeover, data exfiltration, and financial losses from fraudulent payments.
Supply chain attacks impacted 62% of organizations in 2021
- Anchore research ("2022 Security Trends Software Supply Chain Survey")
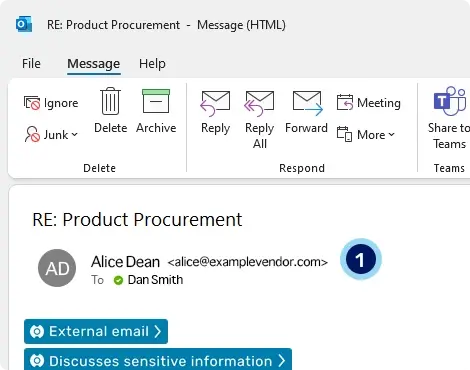
Detecting supply chain attacks
1. Attack launched from a compromised account. The phishing email bypasses Microsoft 365 native security and the SEG as it originates from a trusted domain and the sender and recipient have an established and trusted relationship. In addition, anti-phishing solutions that rely heavily on social graph technology will continue to perceive the account as trusted and won't classify the email as suspicious.
We recognized that one layer is not enough to detect and neutralize the numerous advanced phishing threats targeting GMMH day-to-day work.
Kevin Orritt, Cyber Security Manager, GMMH
Defend provides deep analysis of all indicators of suspicion
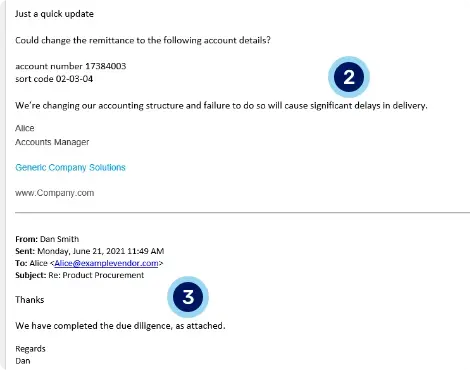
2. Linguistic analysis. KnowBe4 Defend uses natural language processing (NLP) to detect signs of financial information that, when combined with language indicative of repercussions, suggests financial phishing.3. Hijacked existing email chain. The attacker has hijacked an existing email chain that was likely leading to a payment request. This adds an air of authenticity to the email.
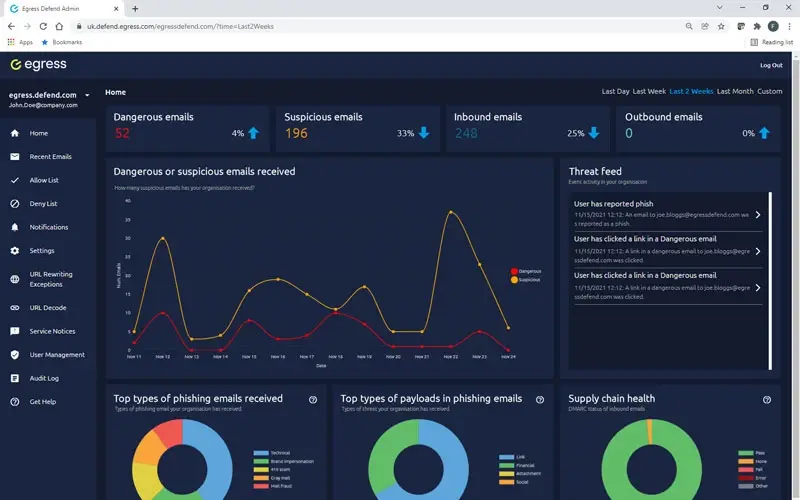
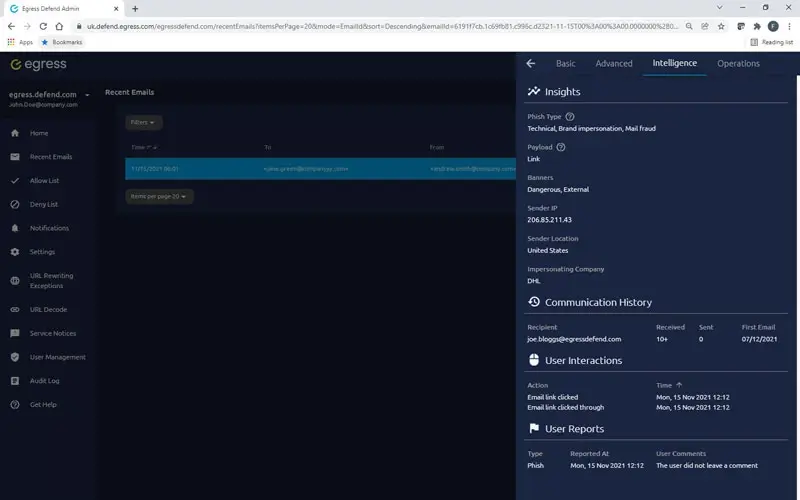
Cut through the noise to highlight the risks that matter
Reporting on threats such as phishing from compromised supply chain accounts within your email flows can be manual and slow. Even worse, systems can throw too much unnecessary information at you, making it harder to make timely and effective decisions.
Defend’s intelligence platform provides simplified dashboards and critical insights so that administrators can quickly cut through the noise, identify email security risks, and, where necessary, remediate them.
Actionable insights
Data and analytics should not overwhelm you with information. Augmented threat intelligence into supply chain health, attack types, and payload gives Security teams what they need to take decisive action that mitigates threats.
Our real-time threat feed offers insights and statistics into email details, type of attack, threat levels, authentication checks, communication history, and how your people interacted with the email.