Invoice fraud is hurting the bottom line
50%
of all money lost to scammers was through invoice fraud
47%
of organizations have experience invoice fraud in the past two years
$40bn
anticipated annual cost of payment fraud by 2027
Undetected invoice fraud can have expensive consequences
Attackers send random invoices through in the hope they'll be paid without second thought, but more frequently they'll socially engineer the victim to make the phish seem legitimate.
Unfortunately, they’re often successful.
71% of organizations were victims of payment fraud attacks or attempts in 2021.
- 2022 AFP Payments Fraud and Control Survey
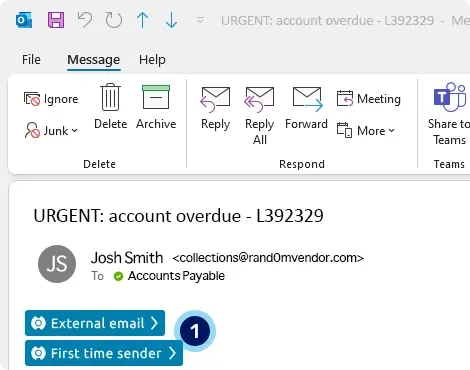
Defend intelligently detects fradulent invoices sent via phishing emails
1. First-time sender. The user has never engaged with this sender before and yet they’re asking for payment. This signal is treated as highly suspicious by KnowBe4 Defend.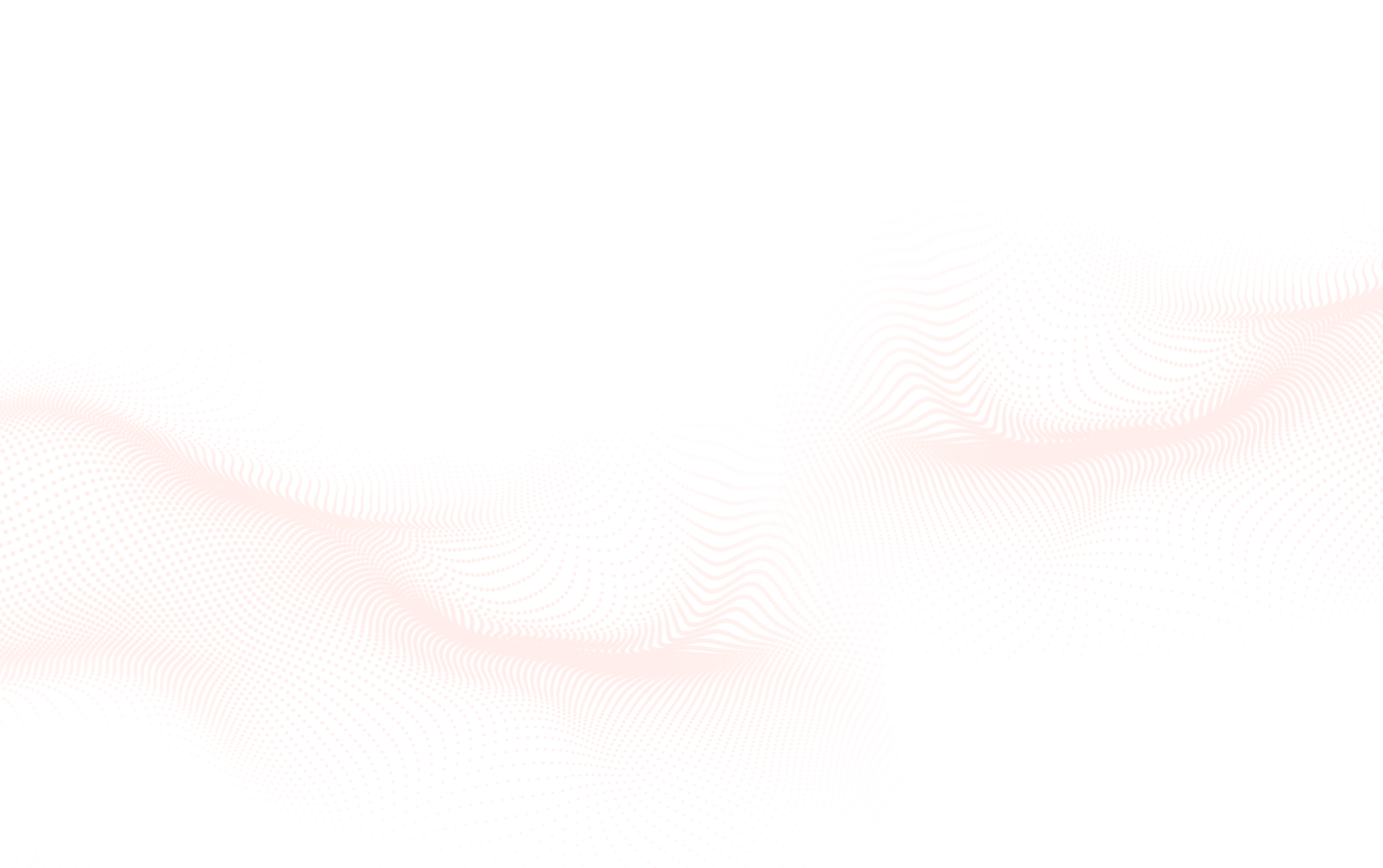
We recognized that one layer is not enough to detect and neutralize the numerous advanced phishing threats targeting GMMH day-to-day work.
Kevin Orritt, Cyber Security Manager, GMMH
Analyze email content for fraudulent payment requests
2. Urgent and financially motivated language. Defend uses natural language processing (NLP) to analyze the content in the email body. Not only is the language financial in nature, but a sense of urgency is added in stating the account is overdue. These, combined with language indicative of repercussions, suggests financial phishing.3. URL analysis. The URL itself could be malicious or it can be a legitimate link redirected on-click. Defend performs link analysis, both at the time of receipt and at the time of click, through link re-writing and protects from delayed, post-delivery weaponization.
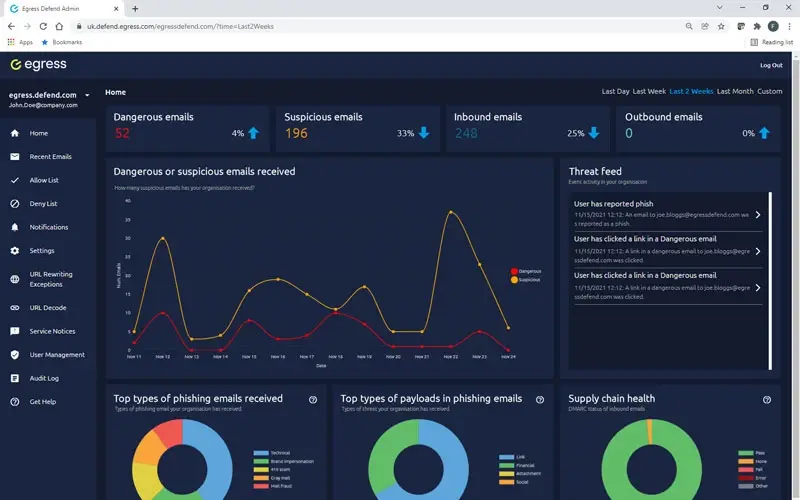
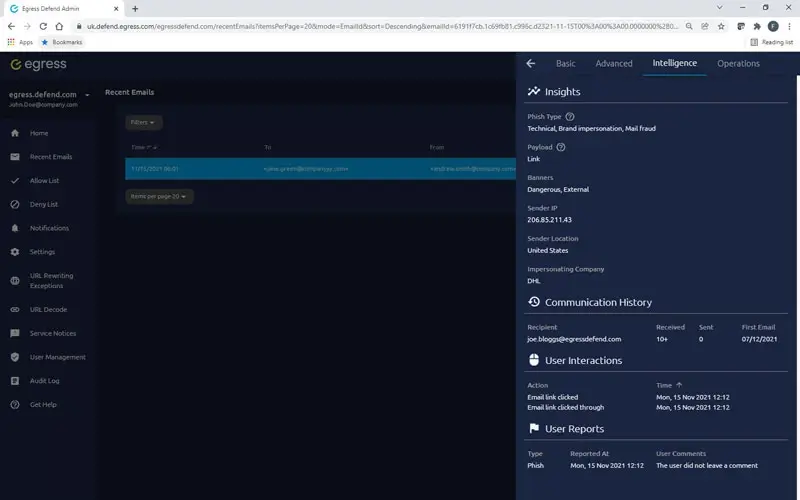
Cut through the noise to highlight the risks that matter
Reporting on threats such as payment and invoice fraud in your email flows can be manual and slow. Even worse, systems can throw too much unnecessary information at you, making it harder to make timely and effective decisions.
Defend’s intelligence platform provides simplified dashboards and critical insights so that administrators can quickly cut through the noise, identify email security risks, and, where necessary, remediate them.
Actionable insights
Data and analytics should not overwhelm you with information. Augmented threat intelligence into supply chain health, attack types, and payload gives Security teams what they need to take decisive action that mitigates threats.
Our real-time threat feed offers insights and statistics into email details, type of attack, threat levels, authentication checks, communication history, and how your people interacted with the email.