Impersonation attacks are one of the most common phishing threats
89%
of phishing emails contain some form of impersonation
52%
of impersonation attacks bypass Microsoft 365 and secure email gateways (SEGs) detection
63%
of CISOs say the threat of deepfakes keeps them awake at night
Detecting impersonation attempts is essential
Impersonation Attacks are a type of social engineering where a cybercriminal poses as a trusted individual, such as a colleague or executive, to gain credibility and deceive victims. These attacks often use spoofed domains or look-alike display names to bypass native security and secure email gateways (SEGs).
Many phishing attacks use sender impersonation to socially engineer their victims by adding credibility.
Cybercriminals have evolved their email impersonation attacks to get through Microsoft 365's native security functionality and secure email gateways (SEGs). This leaves it down to individual employees to determine which emails are legitimate and which are spoofed, with a single mistake exposing organizations to credential theft, data exfiltration, and fraudulent payments.
Over 3 billion spoofed emails are sent every day, accounting for 1% of all email traffic.
- Valimail, Email Fraud Landscape Spring 2021
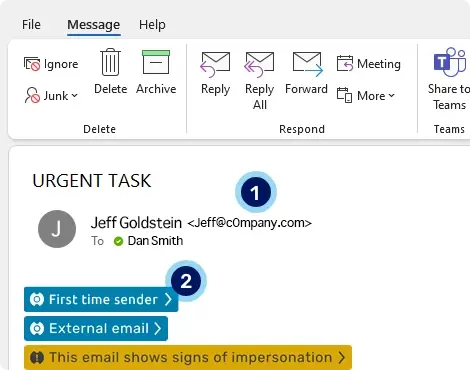
Detecting an impersonation attack using trust and domain analysis
1. Sender domain analysis. The domain c0mpany.com is used to fool the recipient into thinking this is a genuine email. However, the display name matches that used by an internal user. An internal user with an external domain is treated with suspicion.2. Real-time alerts highlight impersonation attacks. Based on its analysis, KnowBe4 Defend highlights to the user that this an impersonation attack sent from an individual they've had no previous contact with.
We’re really pleased with Defend. We’re now detecting a broader range of advanced phishing threats, including BEC and impersonation attacks.
Kevin Orritt, Cyber Security Manager, GMMH
Preventing replies to impersonation attacks
3. KnowBe4 Prevent provides enhanced security to stop replies to impersonation attacks. Outbound emails, including replies to impersonation attacks, are inspected by KnowBe4 Prevent, with alerts that increase intervention to notify the user of the current risk. This further “nudge” will force the user to carefully consider their actions.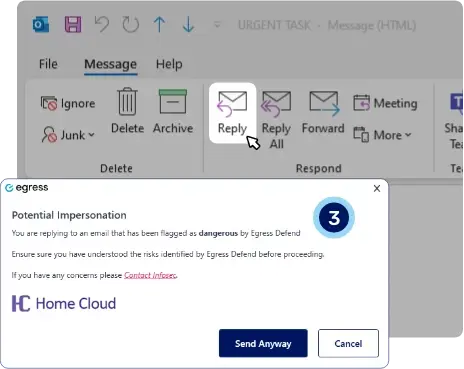
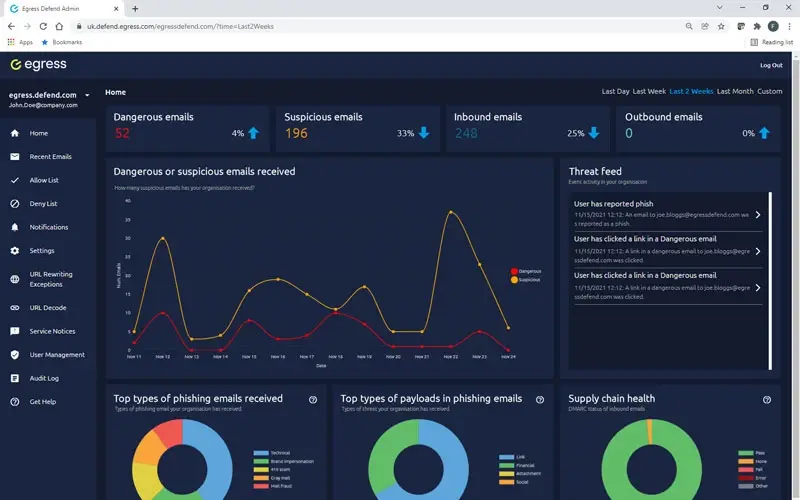
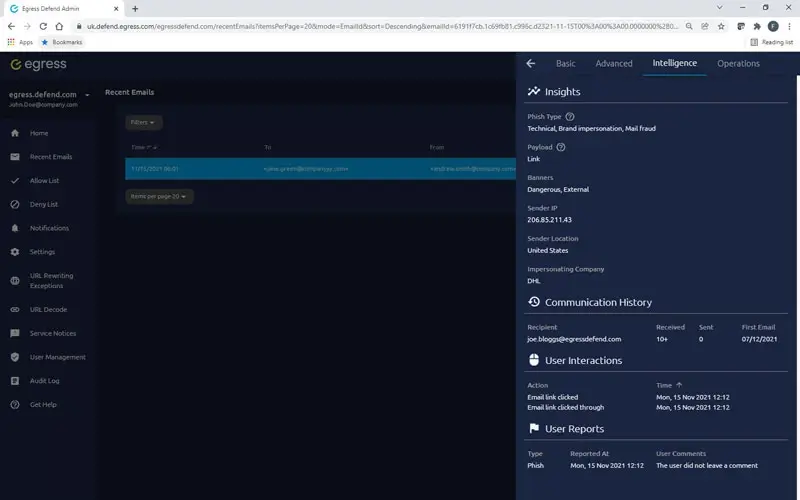
Cut through the noise to highlight the risks that matter
Reporting on threats such as impersonation attacks within email flows can be manual and slow. Even worse, systems can throw too much unnecessary information at you, making it harder to make timely and effective decisions.
KnowBe4's intelligence platform provides simplified dashboards and critical insights so that administrators can quickly cut through the noise, identify email security risks, and, where necessary, remediate them.
Actionable insights
Data and analytics should not overwhelm you with information. Augmented threat intelligence into supply chain health, attack types, and payload gives Security teams what they need to take decisive action that mitigates threats.
Our real-time threat feed offers insights and statistics into email details, type of attack, threat levels, authentication checks, communication history, and how your people interacted with the email.