2025 International Phishing Benchmarks
North America
TABLE OF CONTENTS
2025 International Phishing Benchmarks
North America
By Erich Kron
It’s never pleasant to see the initial PPP for the region; however, it is reassuring to see how quickly the numbers can be reduced. This is a testament to the need for a robust SAT program.
”North America is a target and has been for many years. This is not going to change, so we must counter the threat aggressively and seriously.
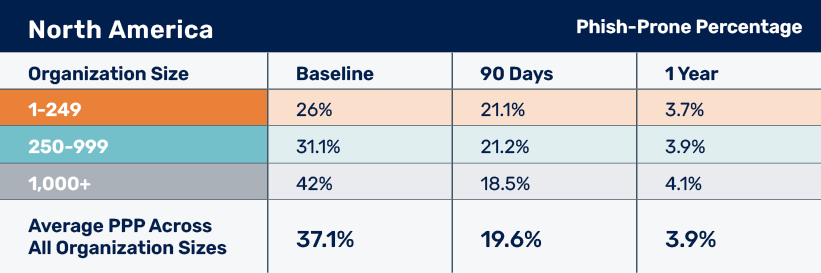
This year seemed to be especially challenging for larger organizations, which had a pretty significant initial click rate of 42%. Even mid-size organizations seem to struggle with an initial click rate of 31.1%, while smaller organizations were reasonably close to other regions at just shy of 26%.
Put into perspective, this means that in large organizations, more than two out of every five users clicked on simulated phishing attacks.
It’s no secret that phishing emails are one of the top threats to organizations across industries. With click rates this high, it is clear that employees are not likely to be looking for social engineering attacks without some guided direction from the organization.
The real success story is how quickly these numbers can improve. Large organizations showed small and medium peers how it’s done — with that 42% click rate plummeting to 18.5% after only 90 days of best-practice SAT. While small and medium organizations also showed remarkable reductions, the large organizations took home the prize at the 90-day mark.
Continuing with the trend of plummeting click rates, across all organizations, the average PPP after at least one year of training was 3.9%. This finding underscores the significant improvement that SAT can effect within any organization. Meanwhile, let’s not lose track of the fact that in typical organizations, the simulation emails employees receive a year after starting the program are almost always significantly tougher than those they received at the beginning.
While click rate is not an all-encompassing measurement, the improvement rate is a strong indicator that employees are paying attention more and have greatly improved their ability to spot social engineering.
The importance of SAT and improving resilience to cyberattacks is a key initiative in North America. According to Intel 471’s 2024 Annual Threat Report, the U.S. and Canada are the #1 and #2 most-targeted countries by ransomware. The truly stunning part is that the U.S. accounted for 51.7% of the 4,205 global attacks analyzed. This is certainly not the kind of attention a country wants.
Social Engineering is a Mental Game
Social engineering — the primary way ransomware spreads and the key factor behind BEC attacks and other phishing/vishing/smishing attacks — is an attack on human emotions.
Cybercriminals twist emotions to the point that we fail to see red flags and do things we wouldn't normally do. The hyper-partisan political landscape in the U.S. and Canada has left people in a heightened state of stress and emotion. This makes it easier for bad actors to get people riled up to the point of making errors. As humans, we simply are not good at choosing wisely when emotionally charged, and this is a major reason social engineering is so effective.
Emotional and Mental Exhaustion are the Enemy
When we are emotionally drained, we are far less likely to push back on a text message claiming we have an outstanding toll due, or an email saying that our account credentials have expired and we need to re-enter them. With the mental exhaustion we can feel after dealing with political matters at home or on social media, it becomes easy to go into a form of System 1 thinking while at work. In this state, we are much more likely to robotically process tasks than to question them when something is slightly out of the ordinary.
Layoffs and hiring freezes can also leave employees more tired and affect morale as organizations push to do “more with less.” Employees may be rushing through tasks just to stay ahead of them, which can also lead to mistakes. Some of these effects can be noted in industries such as Healthcare & Pharmaceuticals, which had a 54.8% initial click rate within large organizations (1,000+ employees) in North America. These are very intelligent people, but the pace at which they work can be detrimental to an employer’s cybersecurity standing. Education also tends to suffer, as well, as funding is generally not strong, and many educators are stretched very thin.
Tools and Education Can Make the Difference
These trends can be countered very effectively by ensuring employees are made aware of the threat, provided the education to spot the threats and have tools deployed to help them identify potentially missed threats. This means consistent, short and impactful education; simulated attacks; and tools designed to help the user understand why certain emails are dangerous, including offering hints that something may be suspicious. Using these methods, the large organizations in healthcare in North America dropped from that staggering 54.8% click rate to an impressive 3.7% in just one year. Results like these show how much an SAT program can affect one of the biggest cyber threats organizations now face.
”The human risk part of an organization's cybersecurity plan must be robust and ongoing to counter the threat of data breaches, financial losses and ransomware across industries
Key Takeaways
No matter how you slice it, organizations across industries in North America are significant targets for ransomware and other cyberattacks.
- Due to political and economic issues, people are tired and emotionally drained, and many organizations are asking their employees to do more faster to remain competitive. These factors make social engineering much easier for bad actors and more difficult for organizations to defend against.
- North America is one of the most targeted regions for cyberattacks, meaning organizations need to take the human risk portion of their cybersecurity programs very seriously
- Our results show how significantly education and training, along with some practice, can reduce employee click rates. Given the size of the phishing and social engineering threat, there are few things that can be done to make such a dramatic difference for so relatively little fiscal investment.