2025 International Phishing Benchmarks
Europe
TABLE OF CONTENTS
2025 International Phishing Benchmarks
Europe
By Martin Kraemer
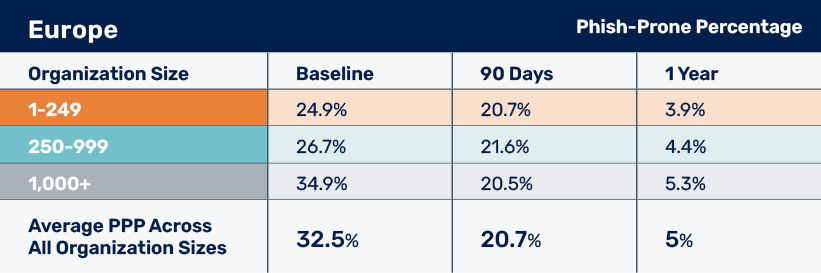
The PPP in Europe remains consistent with the results of previous years. The average initial PPP before implementing SAT is 32.5%, dropping to 20.7% after 90 days and 5% after one year.
As we’ve seen with wider global trends, the baseline PPP is higher in larger organizations (1,000+ employees) at 34.9%, 26.7% for midsize (250-999 employees) and 24.9% for small (1-249 employees). Predictably, larger organizations experience the greatest risk reduction. After one year-plus of training, click rates dropped to just 5.3% — an 84.8% decrease. Smaller organizations achieved marginally lower clicks after one year of training at 3.9% for those with 1-249 employees and 4.4% for those with 250 to 999.
This range of 3-5% PPP has now established itself as the gold standard, and it’s incredibly positive to see European organizations maintaining their averages within this bracket.
”A PPP between 3-5% after one year of SAT is the gold standard
When compared to the 2024 PPPs, the performance was almost unchanged across all organizations. The baseline performance in Phase 1 was 0.1% better. After 90 days of training, the 2025 PPP was 0.4% worse than last year, and after one year-plus of training, organizations performed 0.5% better as compared to the previous year. This result shows a continued positive average performance across the board, showcasing that investments in SAT have led to a reduction in phishing susceptibility as measured by PPP. These numbers have now stabilized and can be considered the benchmark across Europe.
This ongoing and effective risk management remains an urgent priority. When we analyzed data from KnowBe4 Defend, we noted a 68% increase in phishing attacks and 137% increase in BEC globally between March 2024 and March 2025. With these increases come two heightened risks: that employees will be targeted by phishing and that malicious emails will be sent from a reputable address the recipient is likely to trust.
Training Must Match Current Trends and Developments in the Region
Organizations must ensure that phishing training is relevant, personalized and adapted to a person’s job profile, personal circumstances at work and home, and individual risk profile.
Organizations that have not already done so must elevate their training regimen this way to match the quickly changing threat landscape. Denial-of-service attacks and ransomware remain the top threats in the region, with cybercriminals leveraging geopolitics as themes and motivational drivers for campaigns. KnowBe4 has also observed a sharp increase in the quantity and quality of BEC attacks in addition to leveraging reporting deadlines as extortion tactics and AI tools as co-authors of emails and malicious PowerShell scripts.
How many simulated phishing emails are tailored to these threats — and how quickly can an organization pivot to create new training content that simulates real-world threats as the attacks they face change? Without implementing this in best-practice SAT, it’s not possible to fully prepare your people and reduce phishing click rates.
We Must Combine People, Process and Technology to Protect Our Organizations
Last year, the British engineering firm ARUP fell victim to a phishing scam through its Hong Kong branch. The scam notably involved an invitation to an online meeting during which urgent financial matters were discussed. The monetary loss for the organization was significant, showing that awareness of threats and good process are essential to protect organizations. The attackers had worked around both.
In another example, a senior manager at the luxury sports car manufacturer Ferrari demonstrated great knowledge of processes that safeguard payments along with quick wit. Confronted with a suspected scammer posing as the company CEO, this senior manager challenged the caller to name a personal book recommendation the real CEO would have been able to cite.
These examples show that cybersecurity must involve people, process and technology to effectively reduce the risk of falling victim to social engineering.
”Ticking compliance checkboxes once a year is not the same as improving security in day-to-day operations
Compliance Is Not the Sames as Security, But the Market Is Largely Compliance Driven
New regulations continue to shape the cybersecurity landscape in Europe, with the Network and Infrastructure Directive (NIS 2) and the European Union Artificial Intelligence Act (EU AI Act) setting forth training requirements for SAT and AI literacy.
However, ticking compliance checkboxes once a year is not the same as improving security in day-to-day operations. Organizations that successfully increase their cybersecurity resilience also invest in better processes, such as dedicated support teams for the workforce, positive reinforcement and rewards, and metrics that encourage secure behavior.
Key Takeaways
- Established PPP benchmark sets the standard for organizations, with 32% as a baseline, 20% after 90 days and 5% after one year-plus of training
- Regulatory requirements continue to drive the need for security education and AI literacy, increasing the adoption of SAT
- Email remains the number-one attack vector for social engineering, carrying all kinds of payloads, including ransomware, QR codes and job application scams