Locky ransomware was first seen in February 2016 and is a very sophisticated malware that infects networks via Microsoft Word attachments containing malicious macros.
Threat actors social engineer victims twice, first getting them to open the attachment and then getting them to enable macros in the files. The code is written in VBA and looks a lot like Dridex infections which suggests this new flavor is from the Dridex Bank Trojan gang.
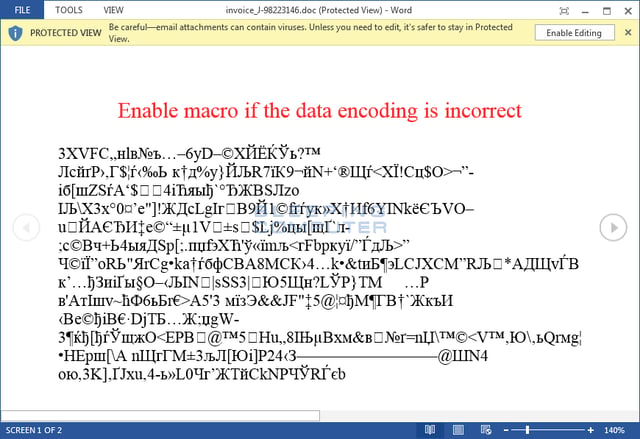
Spear phishing emails in the earliest version of Locky had a subject line like ATTN: Invoice J-98223146 with a message to see the invoice and remit payment according to the invoice terms. The attached Word document even has a message stating to enable macros if the 'invoice' can't be read. As soon as macros is enabled, the macros will download an executable, store it in the %Temp% folder and execute it. Another version seen in May targeted Amazon customers with a message regarding recent orders, again with a Word file attached prompting victims to enable macros.
This strain is spread by Necurs, a sophisticated peer-to-peer (P2P) botnet. Necurs creates its "zombies " by infecting them with the Necurs rootkit. To prevent detection, P2P botnets do not need a lot of traffic between infected computers and C&C servers. Necurs employs a domain generation algorithm (DGA) that allows infected computers to find a new command & control (C&C) when the active one goes down, using an architecture of "nodes" and "workers" where nodes function as C&C servers.
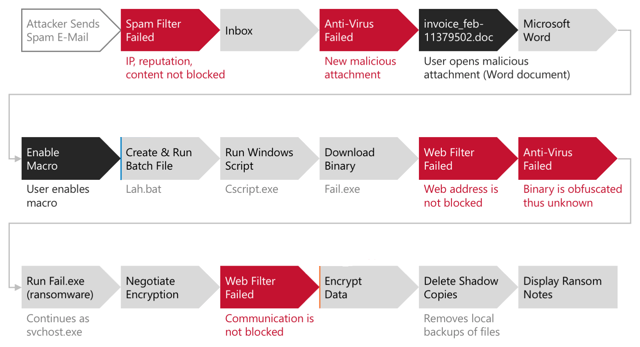
What's significant about Locky is it targets a large amount of file extensions and even encrypts data on unmapped network shares which we have seen previously with DMA Locker. Similar to CryptoWall, Locky also completely changes encrypted filenames making it very difficult to restore correct data. This is a typical attack flow for Locky ransomware:
In June 2016 a new, smarter Locky strain was discovered with a couple of new features. First, it can detect whether it is running within a sandbox test environment versus a live infection. Second, attackers can relocate Locky instruction code in order to make manual analysis of memory dumps more difficult. Another Locky update in July of 2016 allowed the strain to encrypt files offline, meaning shutting down a computer as part of a larger network would not save other machines from being infected. Locky is currently one of the three biggest ransomware threats along with CryptoWall and Cerber.
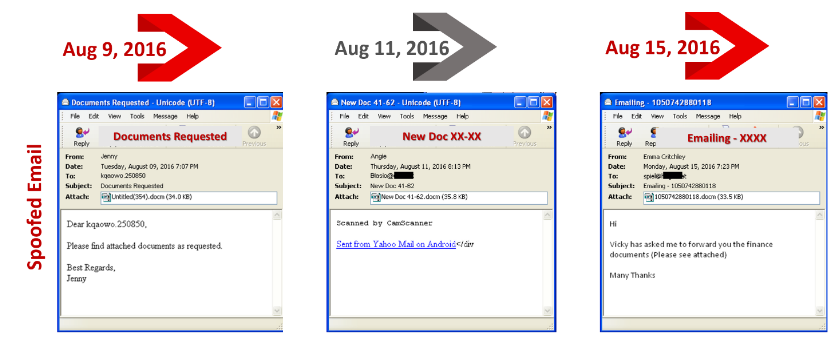
A massive Locky campaign hit America in August of 2016, hitting the healthcare industry the hardest. The emails themselves use DOCM format attachments, and each email has a unique campaign code used to download the ransomware from a command and control server to victim machines. Below are a few screenshots of recent emails found in the wild:
Another phishing attack with the Locky infection came in November of 2016 with emails claiming to be "credit card suspended" and "suspicious money movement" warnings. Here is what the email looks like:
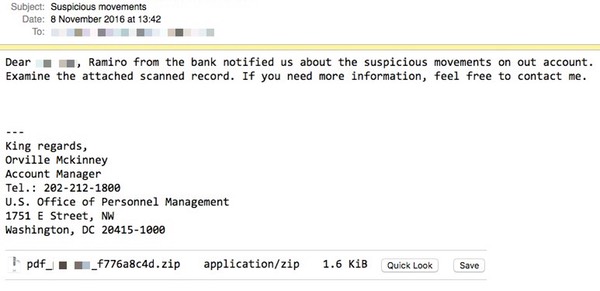
That .zip file you see in the email is a malicious Javascript file (.JS) and if opened, executes Locky.
A new Locky strain called Osiris was spotted in December. The attack vector is another phishing attack with infected attachments. The ransomware executes if the user opens the attachment and enable macros. Here's an example so you know what to watch out for if you get something similar in your inbox:
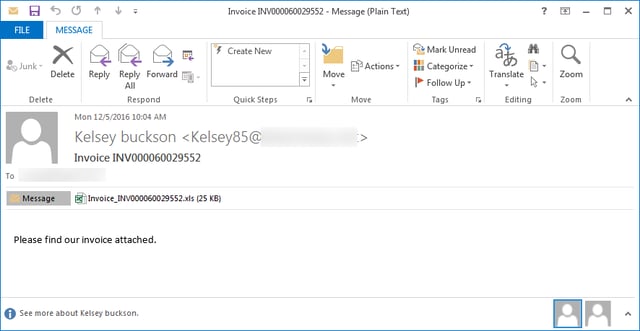
Locky reappeared in April of 2017, this time sending potential victims phishing emails with a PDF that has a Word file hidden within, which then executes a macro script when opened by the user. This scenario allows the phishing email to bypass sandboxes. Here is what this particular attack looks like:
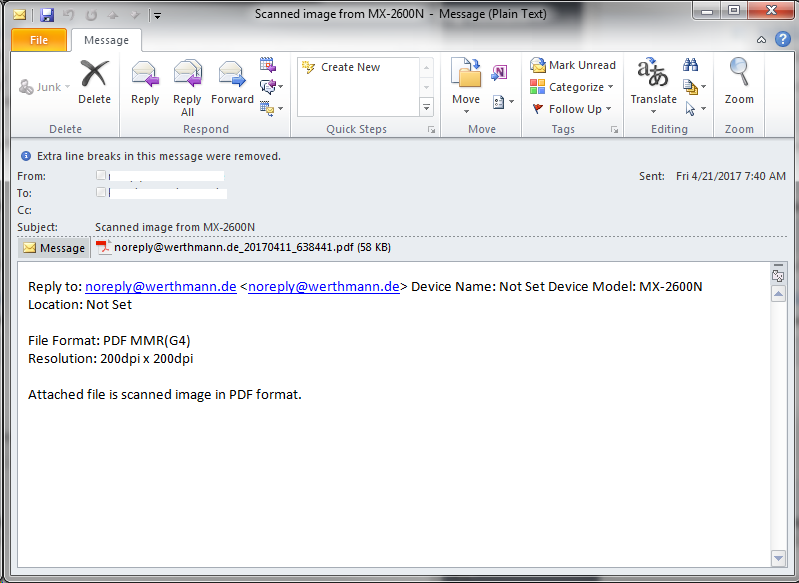
A worldwide campaign spreading the Diablo6 variant came in August of 2017. The emails contain subject lines similar to E [date] (random_numer).docx. For example, E 2017-08-09 (698).docx. The message body simply states "Files attached. Thanks". These emails have ZIP files with the same name as the subject line attached, which contain a VBS downloader script. This script will contain one or more URLs that the script will use to download the Locky ransomware executable to the %Temp% folder and then execute it. Here's an example of a Diablo6 phishing email:
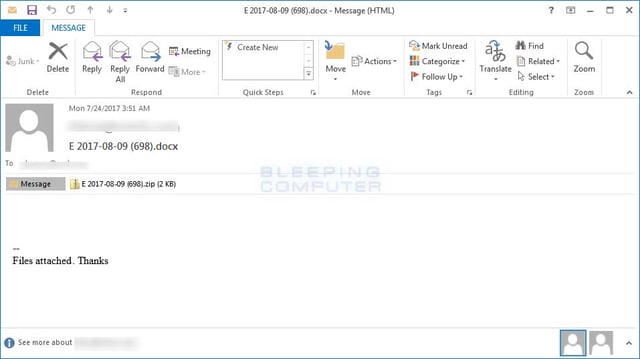
Two new massive Locky campaigns were reported in September of 2017; one pushing a new variant that encrypts files with the .ykcol extension and demanding 0.5 Bitcoin (~$1800) , the other sneaks malicious code into an attachment that looks like a printer output to its victims. The latter allows it to slip past many of the machine learning algorithm-based software sold by some of the industry’s most popular vendors.
