Cerber ransomware was found in March 2016 and actually talks to its victims. It is being offered as Ransomware-as-a-Service on Russian forums so pretty much anyone can use it without coding experience.
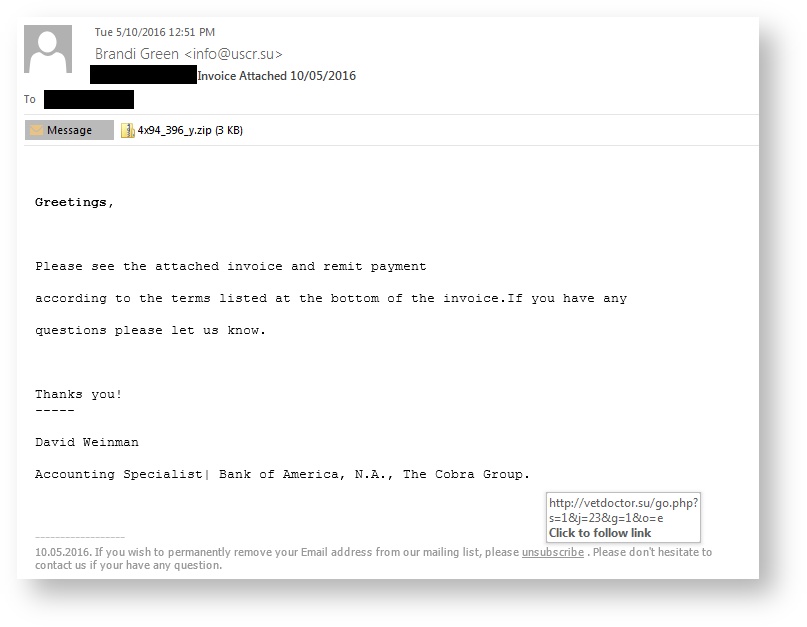
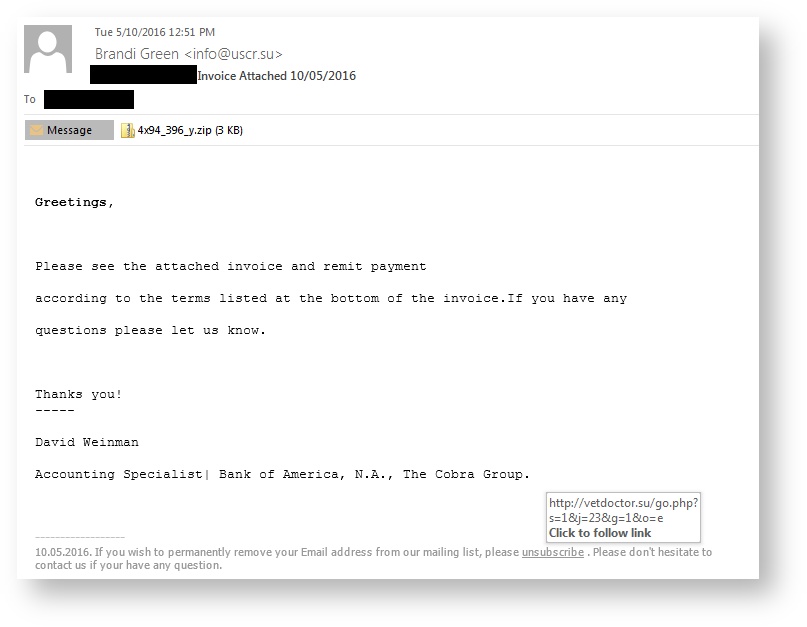
The hackers get victims to download Cerber with two methods; first is a double-zipped file with a WSF (Windows Script File) inside attached to the malicious email, the second is an unsubscribe link located at the bottom of the phishing email, which also links to the same ZIP file. This new strain was also pushed by the Rig and Magnitude exploit kits which both are using 0-day vulnerabilities.
Cerber will first check to see which country a victim is from. If the infected computer is from any of the following countries, it will terminate itself and not encrypt the computer: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan. If the computer is from any other country, Cerber will install itself and name itself after a Windows executable.
Cerber will then start automatically when you login to Windows, execute as your screensaver when your computer is idle, and execute itself once every minute showing a false system alert. When the system is restarted, the computer will reboot into Safe Mode with Networking and once you login, will automatically shutdown again and reboot back into normal mode. Once it is booted into regular mode, the ransomware executes to begin the encryption process using AES-256 and RSA encryption. It will scan for any unmapped Windows shares and encrypt 442 different file types found there.
The ransomware then drops three files on the victim's desktop named "# DECRYPT MY FILES #." These files contain instructions about the ransom amount and how to pay it, one of the three files contains a Visual Basic Script that converts text into an audio message stating what happened to your files. Ransom is currently 1.24 bitcoins or around $500.
There is a free decryption method for the earliest version of Cerber, unfortunately one does not exist yet for newer versions. An update to Cerber in May added a DDoS bot, making it the first time DDoS malware has been paired with ransomware. This adds another revenue stream for the criminals so it is very likely to become a trend.
Just a couple months later in May of 2016, it was discovered that a Russian hacking forum started selling the Cerber ransomware as a RaaS (ransomware-as-a-service). Hackers get victims to download Cerber in this instance using two methods; first is a double-zipped file with a WSF inside attached to a phishing email and the other is an unsubscribe link located at the bottom of the message, which is also linking to the same ZIP file:
 A new Cerber variant seen in May showed off a new malicious skill: it now adds a DDoS bot that can quietly blast spoofed network traffic at various IPs. This is the first time DDoS malware is bundled within a ransomware infection. The attackers use Visual Basic to launch a file-less attack, and most antivirus and “next-gen” antivirus vendors are completely blind to file-less attack methods. What this means is that they are unable to see this thing until it has been dropped on the disk. At that point scanners can find it, and many do, but often that's too late. The infection vector is phishing with weaponized RTF documents.
A new Cerber variant seen in May showed off a new malicious skill: it now adds a DDoS bot that can quietly blast spoofed network traffic at various IPs. This is the first time DDoS malware is bundled within a ransomware infection. The attackers use Visual Basic to launch a file-less attack, and most antivirus and “next-gen” antivirus vendors are completely blind to file-less attack methods. What this means is that they are unable to see this thing until it has been dropped on the disk. At that point scanners can find it, and many do, but often that's too late. The infection vector is phishing with weaponized RTF documents.
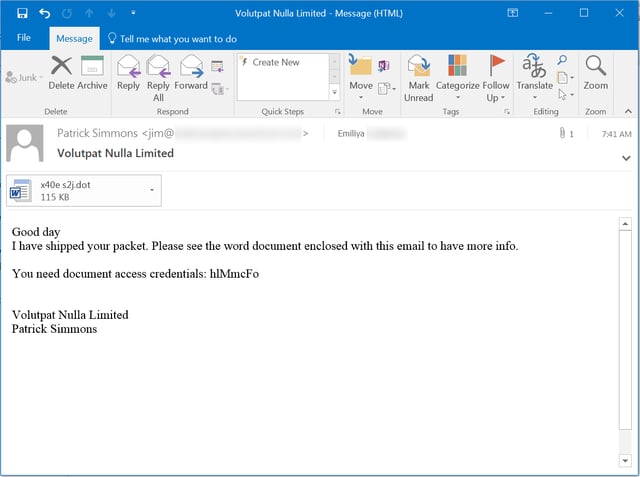
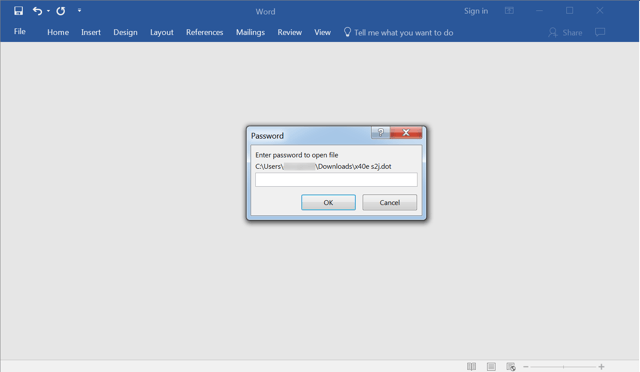
A massive campaign in October of 2016 caused over 150,000 infections. This particular phish started with an attached password-protected .DOT (Word doc template) file. Users who opened the the attachment were prompted to enter a password, which had been provided in the email body. Password-protecting the Word document accomplished two things: encrypting the embedded malicious macro, and giving the user a false sense of security.
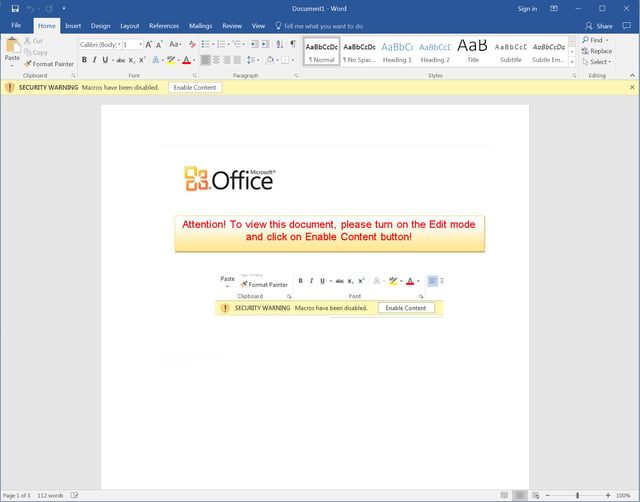
Users who successfully unlocked the document were then confronted with a screen prompting them to click the yellow security warning bar. Enabling the macros executes the Cerber. Here is what this particular attack looks like:
Cerber is currently one of the three biggest ransomware threats, along with CryptoWall and Locky. In fact, even with just 0.3% of its victims paying ransom, the gang behind Cerber and it's affiliates have made almost $200k. If Cerber continues to be successful that would put it on track to make $2.3 million by the end of 2016.
In April of 2017, a new version of the ransomware added techniques to make itself harder to detect by endpoint security software that uses machine learning for detection. It now uses a new loader designed to hollow out a normal process where Cerber's code is run instead. This proves once again that for every new malware detection technique, an equivalent evasion technique is created.
The good news here is this new technique can be defeated by security approaches that employ multiple layers of protection, so solutions that don’t rely too heavily on machine learning can still prove effective against this threat.
Another campaign in August of 2017 lets the Dridex Banking Trojan gang steal from three different Bitcoin wallet apps (the Bitcoin Core wallet, the Electrum wallet app and the Multibit wallet app) as well as steals passwords from popular web browsers including Internet Explorer, Google Chrome, and Mozilla Firefox.
