TorrentLocker is a relatively recent type of ransomware that was discovered as early as February 2014. At a first glance, many unsuspecting victims may mistake TorrentLocker for CryptoLocker. For one, the fact that the ransomware claims to be CryptoLocker, according to the lock screen victims will see when their computers are attacked, is a little confusing. Criminals gangs regularly rip off each other's brands and code, there is no such thing as copyright in the Internet criminals underground.
A closer inspection of this ransomware, according to iSight Partners, revealed that it actually combines elements of CryptoLocker and CryptoWall. However, TorrentLocker’s code is “completely different from these other two ransomware families.” For file encryption, TorrentLocker uses the Rijndael algorithm, rather than RSA-2048.
TorrentLocker is spread through infected spam emails or emails that claim that the victim has to pay for an invoice, a package in the mail, or a speeding ticket fine. And to make things more interesting, the creators of TorrentLocker are mainly targeting specific countries with these infected emails rather than as many countries around the world as possible. As of December 2014, most of TorrentLocker’s victims were located in Turkey, with a total of over 11,000 victims from there, alone. Australia has the second highest number of victims—over 9,000 people—and Italy has the third highest number with over 4,000 people reporting that they have been hit with TorrentLocker ransomware.
The earlier versions of TorrentLocker were actually very easy to crack. Professionals who examined it discovered a loophole that allowed victims to decrypt their own files. However, as soon as the cyber criminals behind TorrentLocker learned about this, they released an even stronger strain that eliminated this loophole, making it highly difficult for victims to do anything other than pay the ransom.
In addition, early versions of TorrentLocker required victims to send an email to the cyber criminals about their predicament and to request the decryption key for payment. In more recent versions of TorrentLocker, everything is done through the victim’s lock screen, which even provides the victim with everything he or she needs to know about bitcoin and how exactly to pay the ransom.
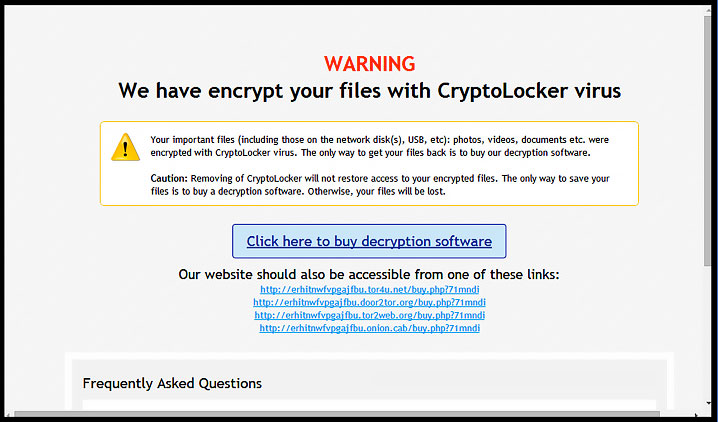
Indeed, the ransom for TorrentLocker can only be paid through bitcoin, and it’s not cheap. Decryption keys for this ransomware have been sold to victims for up to 4.081 bitcoin, which translates to about $1,500. According to ESET, only 1.45% of victims hit with TorrentLocker have paid the ransom as of December 2014. While this might not seem like much, it might surprise you that this small handful of victims has still helped the criminals earn between $292,700 and $585,401 in bitcoins.
Update: TorrentLocker now has a free decryption method available!
