TeslaCrypt ransomware is a copycat of the CryptoLocker strain that infects user's workstations through multiple exploit kits including Angler EK, Sweet Orange and Nuclear EK. An exploit kit (EK) is software designed to locate and exploit vulnerabilities on web servers. They are sold on the dark web, and allows cybercriminals to infect legitimate websites.
TeslaCrypt started by using social engineering to make a user click on a link in a phishing email and later added malicious attachments to those emails. It also used malvertising (malicious ads on legitimate websites) as an attack vector. Victims have been redirected to compromised Wordpress sites that have the Nuclear EK installed, in at least one case it exploited a vulnerability in an out-of-date version of Flash player (13.0.0.182).
In addition to encrypting a list of file types normally targeted by other strains of ransomware, TeslaCrypt also tried to cash in on the gaming market by encrypting over 40 file types associated with popular computer video games, like Call of Duty, Minecraft, and World of Warcraft as well as files related to/from iTunes. In other words: "all your files belong to us".
When a victim is infected, the ransomware looks almost identical to CryptoLocker. It's not until the payment site with instructions on how to pay the ransom comes up that it's obviously TeslaCrypt:
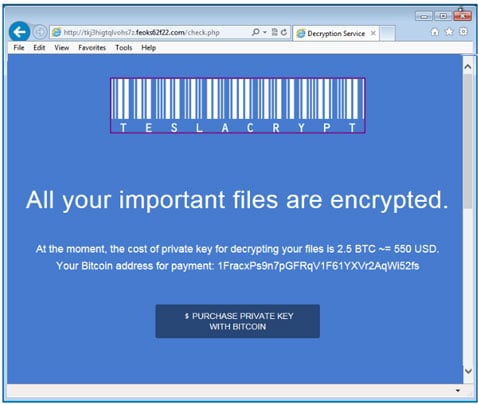
The payment process is run through a website located in the TOR domain. Each instance of the ransomware has a unique Bitcoin address. The files are encrypted by using the AES cipher, and encrypted files gain the .ecc extension.
TeslaCrypt V2.0 was first seen around July 2015 and instead of copying CryptoLocker, this version behaving like CryptoWall in that it's demaning that its victims pay ransom as soon as possible. The new encryption is more sophisticated than V1, a free decryption became available but with V2.0 keys are generated using the ECDH algorithm.
Version 3.01 of TeslaCrypt was updated with unique encryption for each victim, making it impossible to use a master decryption key to use for multiple victims.
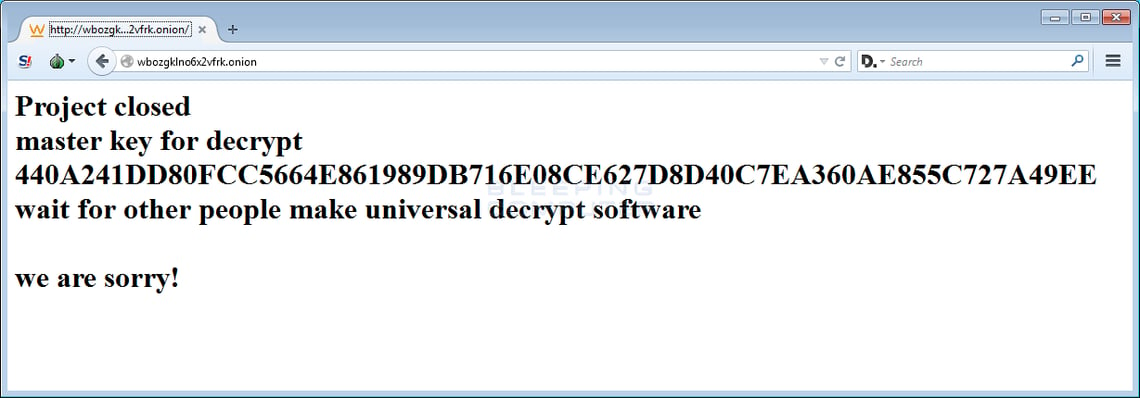
UPDATE: In May 2016 the threat actors behind TeslaCrypt shut down the ransomware and released the master decryption key: