The GPcode ransomware was released in June 2006 infecting PCs through spear phishing scams. The GPcode was spread via email attachments that looked to be a job application.
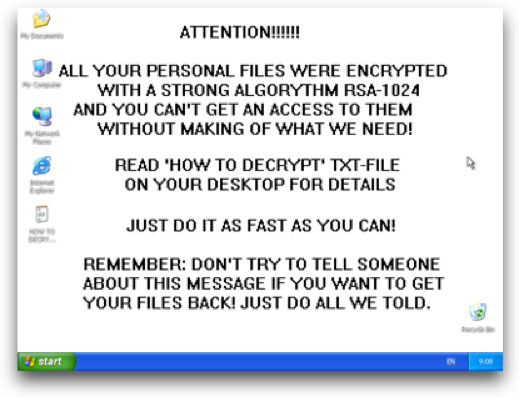
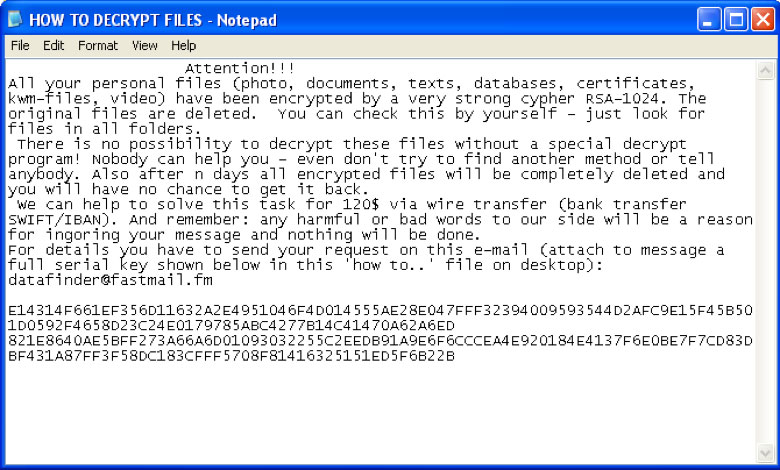
The first versions of GPcode was easily broken because it wrote the encrypted file to a new location, and deletes the unencrypted file, and this allows an undeletion utility to recover some of the files. This sometimes gives enough information to decrypt other files. Other variants or GPCode ransomware use symmetric encryption, which made key recovery very easy.
Using a 660-Bit RSA public key to encrypt or lock victims files, GPCode ransomware would prevent victims from accessing everything in the MyDocuments directory. GPCode required victims to pay a fee or ransom and in return a code or key would be delivered to the victims; which they would used to unlock their files.
This version of ransomware is especially nasty because it can leave a backdoor open to other hackers. Furthermore, this gateway allows hackers to access important information such as secure documents, social security number, bank account numbers and credit card information.
In late November 2010, a new version of GPCode was discovered that uses stronger encryption (RSA-1024 and AES-256) and physically overwrites the encrypted file, making recovery nearly impossible.
