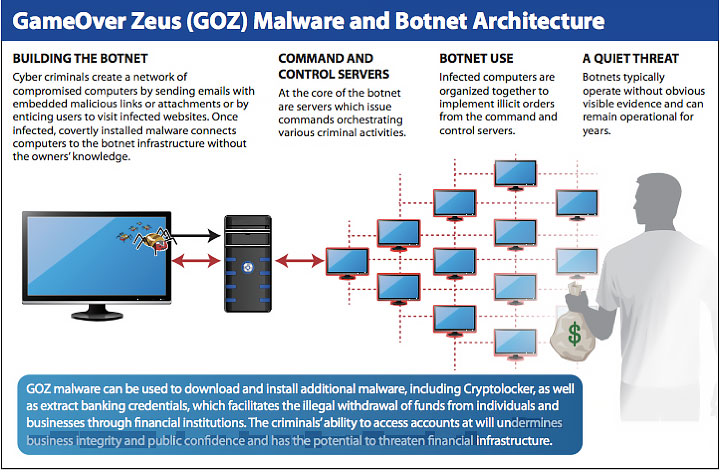
Gameover Zeus is a peer-to-peer (P2P) malware extension of the Zeus family that steals bank credentials and is a distributor for CryptoLocker ransomware. It was first discovered in 2011. Cyber criminals use it to "filter" money away from banking customers. Gameover Zeus is widely considered one of the most advanced variants of the Zeus family tree and unlike its cousins Citadel and IceX Trojan it is not for sale.
Gameover Zeus (GOZ) has withstood at least two previous attempts to disarm the botnet, once in the spring of 2011 and another in autumn of 2012. What made the takedown so difficult is GOZ gang's constant monitoring of any suspicious activity to protect their vast network of existing compromised computers. In short, the gang recognizes that this a lucrative enterprise which is worth protecting and constantly monitors their robust infrastructure. The group has even been known to identify weaknesses and quickly correct them.
Several antivirus software companies continue to monitor the Gameover network and have been trying to cleanup the botnet.
According to PC World, on July 11, researchers from a company called Malcovery Security spotted a new variant of Gameover Zeus that had stopped using a peer-to-peer based command-and-control infrastructure in favor of domain names.
The botnet is primarily used to steal large sums of money through fraud by taking over thousands of banking customers' banking sessions. These fraudulent methods are performed in real time. Additionally, the cyber criminals are crafty and will often distribute the malware via email that looks like an invoice, ultimately tricking the customer into thinking it is from their bank. They are also targeting HR departments through Monster and CareerBuilder in an attempt to set up fake employees and access baking data that way. Once the deed is done the virus has infected the computer and waits until the user accesses their banking website. Gameover then identifies and intercepts their online session using a technique commonly known as man-in-the-browser (MITB). The malware also has the ability to bypass two-factor authentication and can display malicious banking security messages to weasel out secure information to authorize transactions and fraudulently claim their victim's money.
The end goal of the Gameover Zeus group is to make a profit from the fraudulent information they receive from the botnet. The P2P Zeus crew primarily makes a profit from the botnet through large Automated Clearing House (ACH) transactions and wire transfers. In order for this malware ring to function the gang must siphon funds from compromised bank accounts and work with other cyber criminals to complete the transfers. Just like drug cartels, these accomplices are known as money mules and are often located in the same areas as the victims. This reduces the risk of detection and allows them to complete the transaction much more smoothly.
Update: The original Gameover ZeuS/CryptoLocker network was taken down late May 2014, but resurfaced by July 2014. In fact, you didn’t even have to wait for that network to be rebuilt since copycats had already hit the Net. While they generally have a similar overall operating pattern of encryption and extortion, they come from different sets of hackers and each has their own unique characteristics.
