Here at KnowBe4.com, as we began to assemble training materials for Internet security awareness and cybercrime prevention, we sat down and asked ourselves, what would the bad guys do to maximize their return on time and money they invest? After all, they think like businesspeople, too. So we also asked these questions: “What kind of companies would make the best targets for a cyberheist?” and “Why?” We realized that small but fast-growing businesses that focus primarily on rapid expansion and don’t devote a lot of resources to IT security were probably prime targets. Where could we find such an exclusive group? The Inc. 500/5000 lists. (It wasn’t that hard to come up with since I am an Inc. 500 alumnus; in 2001, my IT company, Sunbelt Software made that list.) Better yet, the Inc. website listed the domain names for most of the targets.
Our plan came together in a few minutes. We would scrape the Inc. 500/5000 lists, build a database of domain names, use a free data-gathering service (aka an easily acquired hacking tool) to find all publicly available email addresses that belonged to each domain, and then send them a simulated phishing attack with no malicious payload to see which ones would be easy targets. We ran this by our lawyers and asked how we could do this without getting into trouble. They gave us some tips and said there would be some risks, but because this was a research project, they thought we could explain our way out of problems. They were right.
We scraped the Inc. site, gathering all the company names, locations, sectors of activity, revenues, and numbers of employees. Next, we deployed our data-gathering service and found about 40,000 email addresses, over 3538 companies. Then, we ran a test using only 989 email addresses spread over 81 companies. We used an existing, high-reputation bulk email service to send this test batch, and let them know in advance what we were doing. We used a variant of a phishing email that required the recipient to click a link to indicate they were not spamming government servers. The email was sent by H.J. Granger, CPWP, CHP Compliance Manager, HSWW Government Services. You might recognize the sender’s name and HSWW if you’re a fan of children’s science fiction/fantasy literature.
We had mixed feelings when we saw that, within a few hours, about half of all recipients at these random test companies clicked our link. The landing page we sent them to was a website created for this test at www.phishingresearch.org. On that landing page the recipients were notified they had taken part in phishing research and that all was well.
However, one alert soul reported us to the bulk email service we used (good for you!), and despite our earlier heads-up, that service suspended our account. We called to remind them that this was research, but a company rep said the test bruised the email service’s reputation and that we had to find another solution. We agreed, and the account was turned back on. Next, we resorted to tactics that cybercriminals use for such attacks: we used a one-time mail server with an Internet Protocol (IP) address we were willing to put aside upon concluding the test, and sent our simulated phishing email to the rest of the 40,000 email addresses in our test pool.
Using an email server/IP address with an unknown reputation significantly reduced our delivery success rate, but we were still able to deliver some 28,243 emails. However, we were once again reported (excellent!), and our phishingresearch.org domain was shut down along with its hosting account. Delivery failure reports were still rolling in at the time we were shut down, so we were able to gather data for only about 21 hours in all.
All of the steps we took simply represented low-hanging fruit. If we had spent more time on each step we would have obtained significantly better results. We just wanted to know what percentage of the Inc. 500/5000 might be Phish-prone (that is, vulnerable to a simple phishing attack). This rate turned out to be a whopping 15%! Because there were nearly 500 companies in which employees clicked a link in a fairly transparent phishing attack, we decided to call them the FAIL500. Excluding the extremes on either end of the scale (smallest and largest), the average number of employees per FAIL500 company is about 275, which means they are very likely to keep significant funds in their operating accounts. It’s so easy to be a cybercriminal. No wonder that cybercrime is a growth industry—the criminals would make the Inc. 500 themselves, with ease!
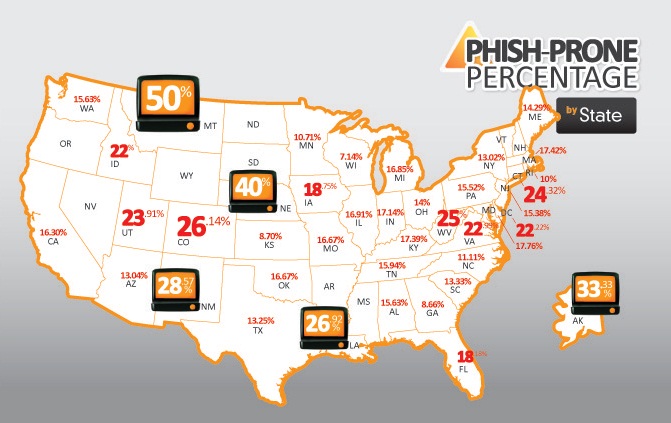
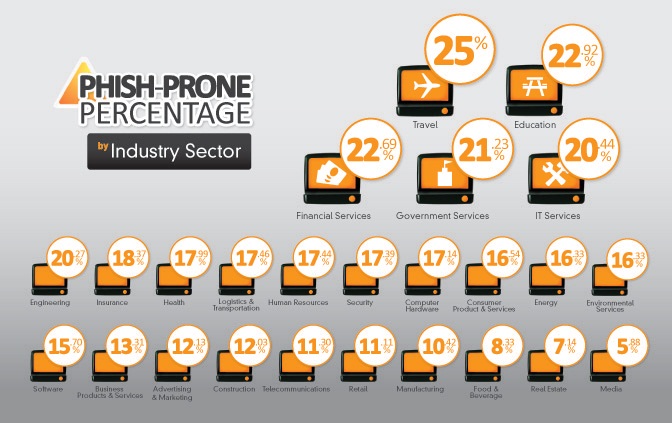
We then sliced and diced our data to determine the best targets (aka the most Phish-prone) by industry, size, location (state), revenues, and number of employees. The picture is not pretty. These are the top 5 Phish-prone industries: Travel 25%, Education 23%, Financial 22%, Government Services 21%, and IT Services 20% (You would think IT would know better!). It can take only one click to cause untold damage, loss of business, loss of cash and massive legal bills.
No individual company is singled out, although we gave a few people a call and suggested that they urgently give their employees KnowBe4 Internet Security Awareness Training! Whatever the ultimate outcome, we couldn’t find a better demonstration of the need for such training, or the likelihood that phishing attacks continue to succeed.
Stu Sjouwerman and the KnowBe4 IT team